DM me for all account retrievals.
Recover locked/lost accounts with ease. #gmailhack #gmaildown #hacked #Hacking #hackaccount
#hacked #facebookdown #WhatsApp #hacked instagram #TwitterDown #lockedaccount #metamask #ransomware #NFTs #crypto



🚨 #BREAKING 🚨RansomHub #Ransomware names Frontier🇺🇸. Revenue: $5.7 Billion.
#DarkWeb #Cybersecurity #Security #Cyberattack #Cybercrime #Privacy #Infosec
Frontier announced that on April 14th, they detected that a third party had gained unauthorized access to portions of its



😱 Las #Pymes son el objetivo principal de una de las mayores #Ciberamenazas a nivel mundial. 🌏
Lucy Bravo nos comparte todos los detalles sobre el modo de operar del #Ransomware . 🪱
➡️ Comparte este contenido para que más personas se mantengan informadas. 🧐


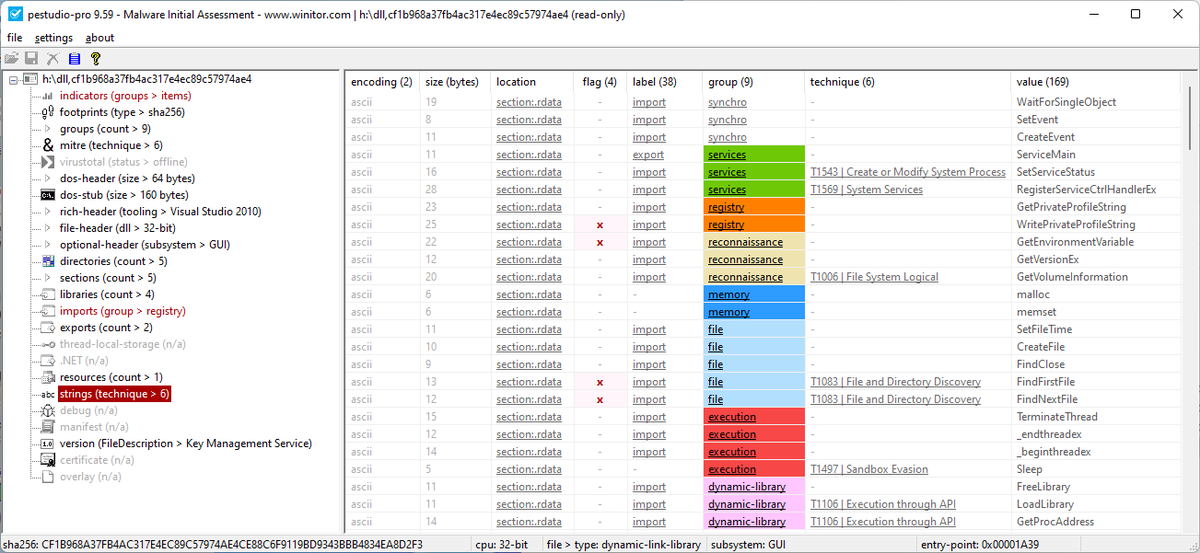
Play #ransomware group has announced 5 new victims on its blog site
#Canada 🇨🇦 (1)
#USA 🇺🇸 (4)
🇨🇦 - NTV Canada
🇺🇸 - FPL Food
🇺🇸 - Walser Automotive Group
🇺🇸 - Elmhurst Group
🇺🇸 - Credit Central
#DarkWeb #cyberattack
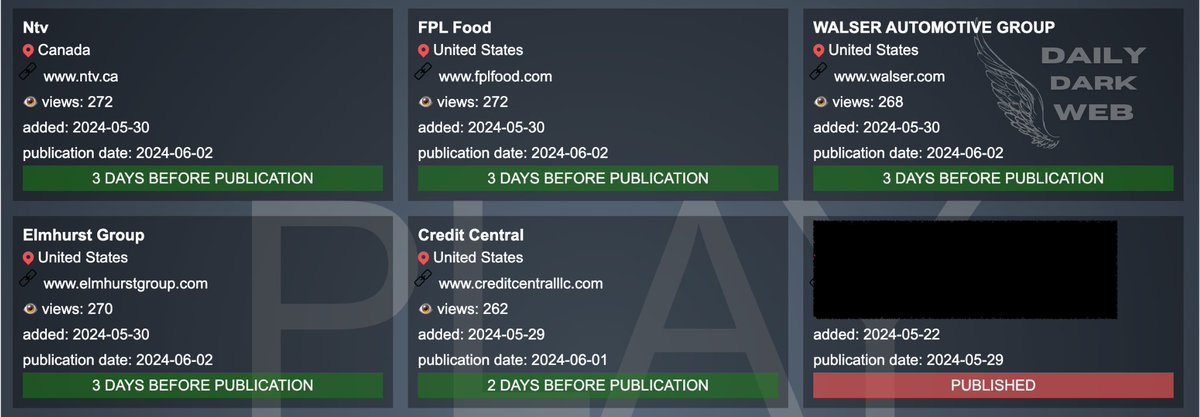



🚨 #CyberAttack 🚨
🇪🇸 #Spain : Ayuntamiento de San Lorenzo de El Escorial has been listed as a victim by the LockBit 3.0 ransomware group.
The hackers allegedly exfiltrated 450 GB of data.
Ransom deadline: 13th Jun 24.
#Ransomware #LockBit
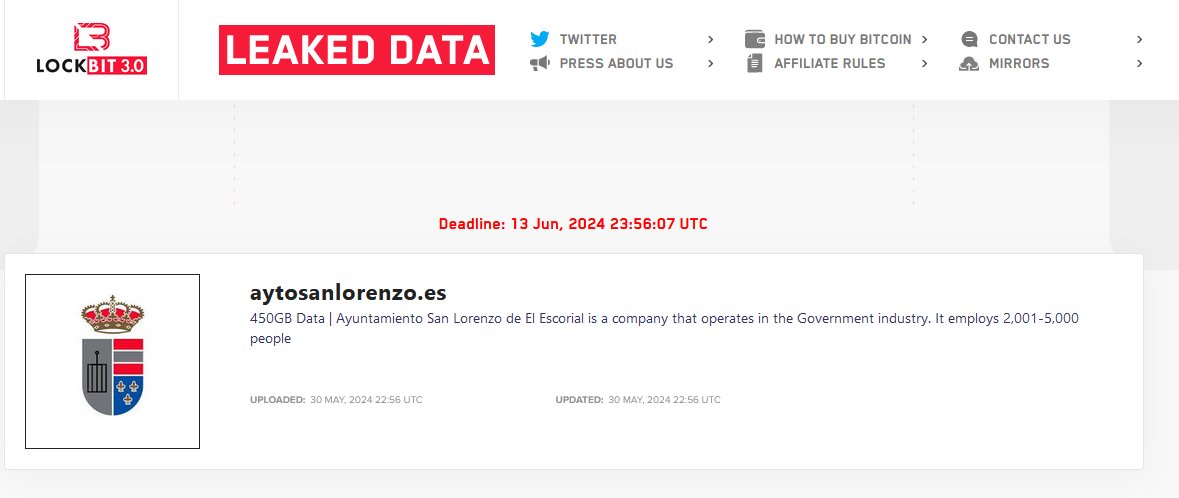

Today RansomHub ransomware group claimed to ransom Frontier Communications. Frontier Communications is a large Internet Service Provider based out of Dallas, Texas.
Frontier Communications confirmed this by submitting a form 8-K to the SEC.
Information via Dominic Alvieri



L'importanza delle ricerche e delle analisi è cruciale quando ci sono di mezzo soldi, reputazione e posti di lavoro.
Ho già parlato di come basarsi su quello che un gruppo #ransomware scrive, non deve essere oro colato.
Serve controllare, andare a fondo e verificare.
Perché se

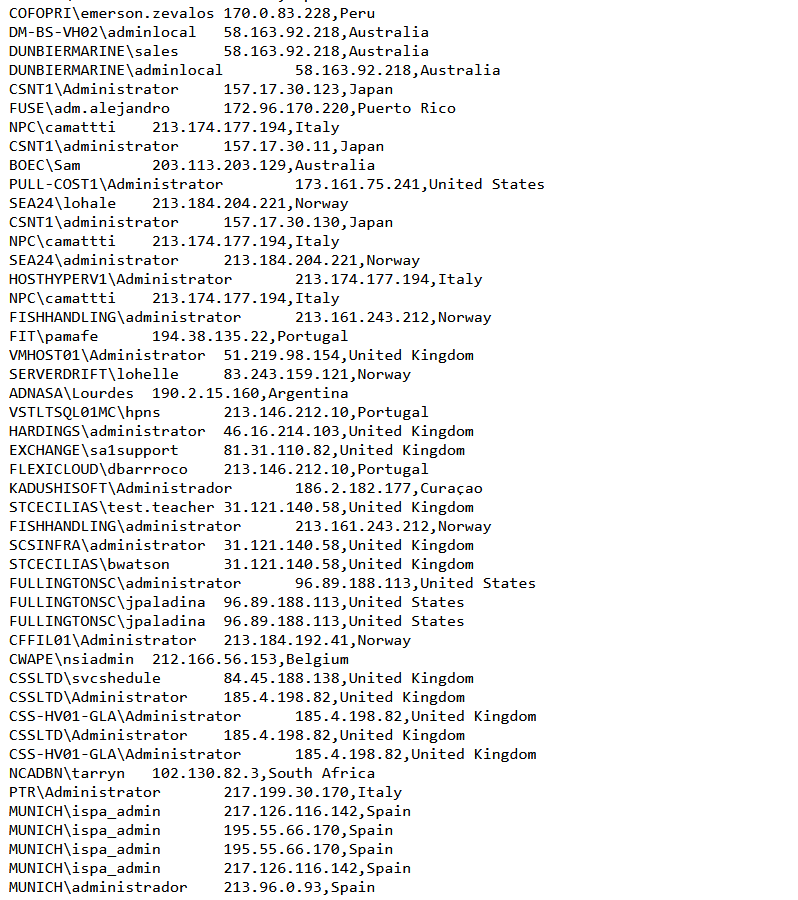
![Efstratios Lontzetidis (@lontze7) on Twitter photo 2024-05-30 13:54:51 leaked #Mallox #ransomware builder and files??
http://185.73.125[.]6/ leaked #Mallox #ransomware builder and files??
http://185.73.125[.]6/](https://pbs.twimg.com/media/GO1Ooi8WkAA9Swo.png)