Are your connected smart devices compliant?
Media release: gov.uk/government/new…
Cyber Trust Mark: iotsecuritytrustmark.org
#psti #iotsecurity #psti #cybertrustmark #cybersecurity


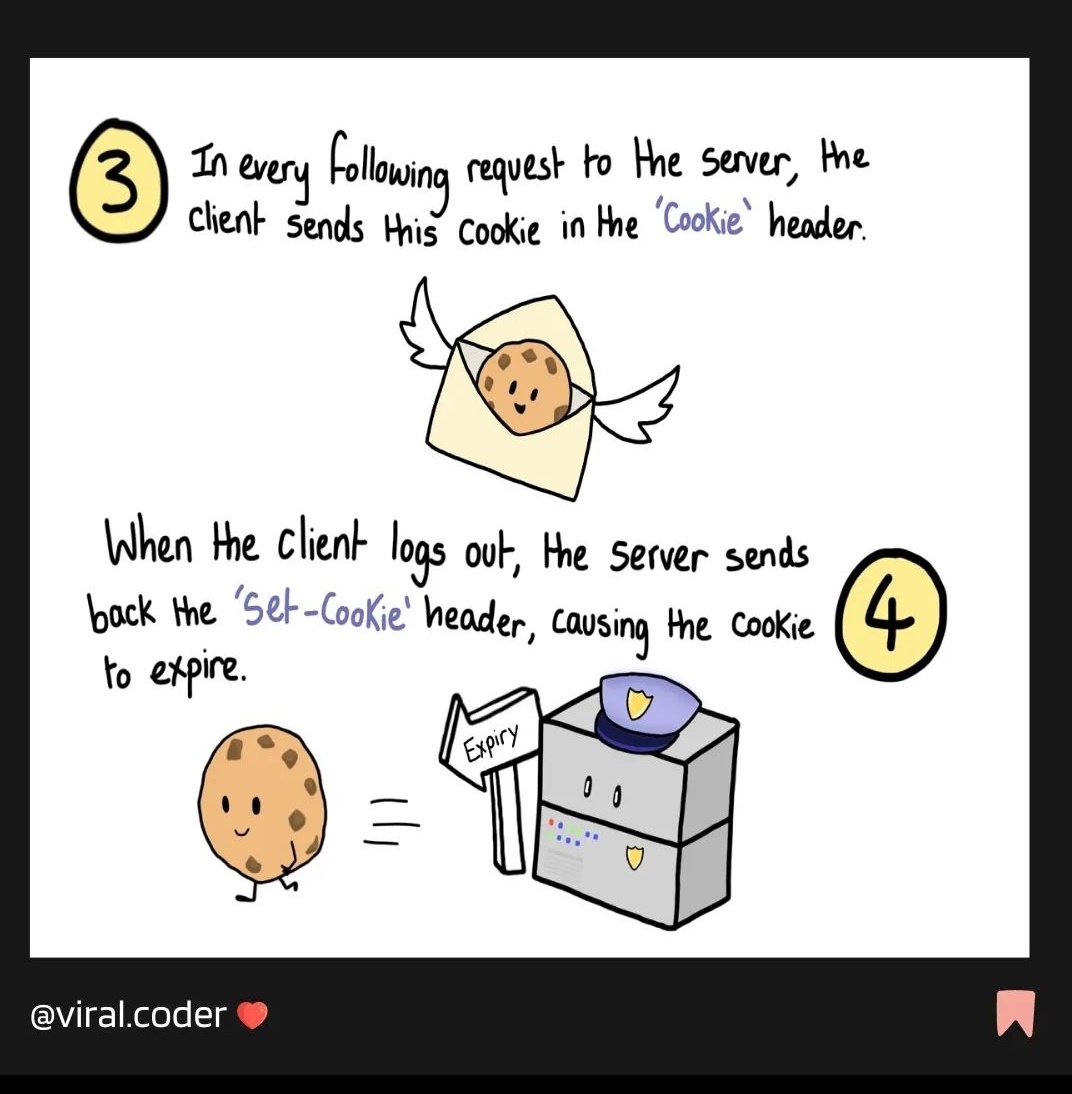
Cookies based Authentication 🛡️
Follow Cyber Security Edition
#Cybersecurity #InfoSec #CyberAttack #DataBreach #Ransomware #Malware #Phishing #CyberCrime #Hacking #Security #CyberThreats #IoTSecurity #CloudSecurity #CyberRisk #DataProtection

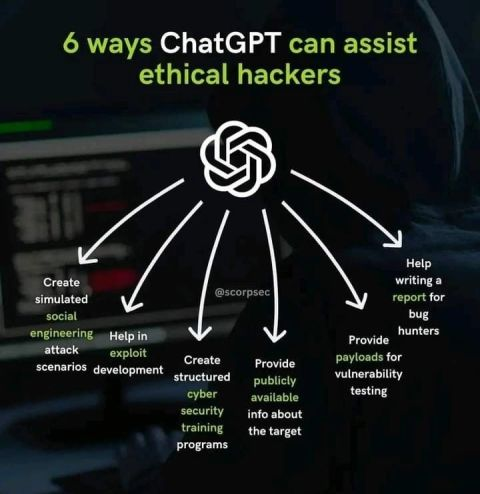
6 ways ChatGPT can assist ethical hackers
Follow Cyber Security Edition
#OpenAI #Cybersecurity #InfoSec #CyberAttack #DataBreach #Ransomware #Malware #Phishing #CyberCrime #Hacking #Security #CyberThreats #IoTSecurity #CloudSecurity #CyberRisk #DataProtection

Discover the world of CAN Bus—a crucial communication protocol in vehicles and beyond.
As CAN hacking rises with IoT advancements in automotive, this video explores security testing for CAN-enabled devices.
➡️ youtube.com/watch?v=m4sdfu…
#infosec #iotsecurity #hardwarehacking

🏍️ Watu Africa & Nodle team up to boost boda boda security in Africa! 🏍️ Blockchain & IoT tech for real-time tracking in Uganda, expanding across 6+ countries. #WatuAfrica #Nodle #BlockchainTechnology #IoTSecurity #BodabodaSafety #AfricanInnovation #TechForGood




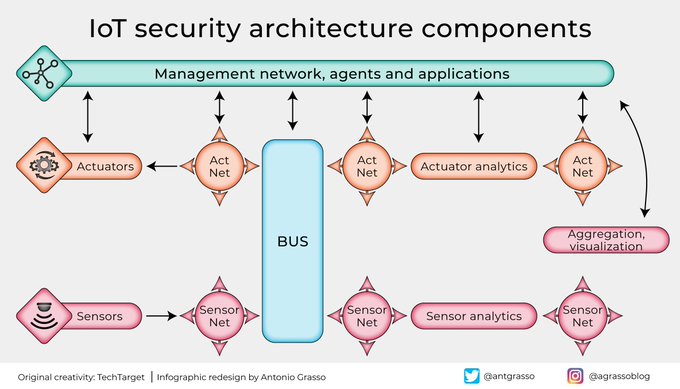
#IoT device security is vital for safe adoption. Yet, it's often misunderstood, even by experts who view IoT devices as black boxes. #infographic !
RT Antonio Grasso
#IIoT #CyberSecurity #IoT Security #TechSafety #tech nology #tech #ai #internetofthings #automation #innovation

Today we continue our smart camera #hacking series! Follow along as Andrew extracts firmware from the camera's board. In Part 3, he'll unpack the firmware & look for the password.
Ideas on smart devices we should hack? Let us know!
#IoT security #hardwarehacking #IoT

🔒The edition of Financial Express publishes an article by Venkatesh Sundar (Founder and President, Americas, Indusface) where he underscores the criticality of cyber risks in the 5G era.
#securitynews #telecomsecurity #cybersecurity #iotsecurity #api #cyberrisks #cyberthreats


Hack a smart camera with Andrew! 📷
Watch as he walks through his process in this clip, the first installment of a multi-part series; this time, his focus is on finding a shell.
Part #2 coming soon 🔜
#IoT security #hardwarehacking #IoT

'Building on the foundation of #Matter , we've re-envisioned Google Home as a platform for developers - all developers, not just those that build #smarthome devices.” Matt Van Der Staay, Google for Developers
bit.ly/3K2GK1i
#csaiot #standardsmatter #iotsolutions #iotsecurity

📙 Flash Networks` May 2024 update
#mobilenetworks #mobileoperators #innovation #mobiledata #mobiletechnology #telecommunications #cybersecurity #iotsecurity
#enterprisesecurity #smartcity
shorturl.at/esATV


#Regulators are coming for #IoT device security
buff.ly/3wCKbsl
@HelpNetSecurity @BaldassariFr Memfault #tech #IoT Security #cybersecurity #digital #innovation #leadership #CISO #CIO #CTO #CDO #OT #OT security #ICS #IIoT #IndustrialIoT #devices #sensors #data #regulation

Wanna obtain the FIRST certification in Embedded Hardware Security & become Certified Hardware Hacker?
👉Checkout whid.ninja ❗🏴☠👈
#CertifiedHardwareHacker #HardwareHacking #IoTsecurity


Transforming Your Home: The Benefits Of A Smart Hub
#smarthome #smarthub #homeautomation #hometechnology #connectedhome #futureofliving #hometechnology #HomeInnovation #SmartLiving #IoTSecurity
tycoonstory.com/transforming-y…

Building a hyper-resilient cyber strategy is crucial in today's digital world! Learn about key considerations for protecting your organization from cyber threats. Stay ahead with proactive measures and robust security practices.
#CyberSecurity #IoTSecurity #SaudiVision2030